Protecting the information and intellectual property of our clients is a principal objective of Beacon’s products and services. As a cloud-native platform, Beacon has invested in leading security measures at every point of the platform’s development, deployment, and operations.
Our comprehensive cloud infrastructure, financial engineering tools, and transparent source license are innovation accelerators, enabling quantitative developers to securely integrate with existing systems and build, test, and deploy cloud-native financial services applications with confidence.
Security in the cloud has some different challenges from security in data center or on-premise operating models – protecting data and intellectual property while getting the full benefits of cloud infrastructure and elastic compute capabilities
A security model with two elements that span product planning through client operations, and work together to deliver the highest levels of protection:
Segregated and controlled cloud infrastructure that forms the backbone of our platform, delivering the security, scalability, speed, and connectivity financial services firms need to build differentiating strategies and develop a competitive edge
DevSecOps (Development, Security, Operations) is a combination of culture, processes, and technologies that treats security as an integral part of and shared responsibility throughout the entire software development lifecycle.
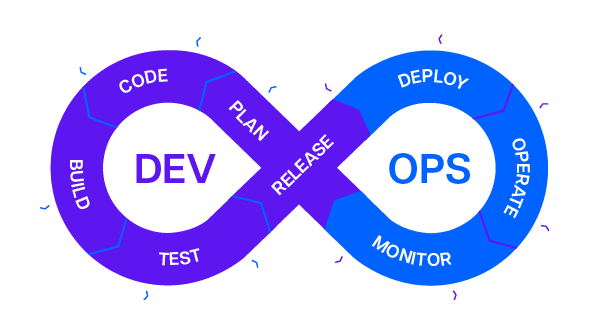
Beacon’s DevSecOps processes are supported and automated by the company’s integrated development environment (IDE), which is based on Visual Studio Code (VSCode). Standardization and automation of development and deployment workflows enhances compliance with best practices, company controls, and regulatory requirements.
By providing an enterprise-class developer experience with robust controls, we ensure that data, code, and intellectual property are always protected, so developers and quants can focus on building differentiating tools and strategies.
Beacon Cloud follows the shared responsibility model between cloud provider, Beacon, and customers that leverages the capabilities and resources of each participant to deliver effective security coverage. Cloud infrastructure has been certified and is in use by major organizations around the world, including for data and workloads covered by stringent privacy and confidentiality regulations and top-secret classifications. Data is protected by encryption at rest and in transit, with client-specific and managed keys.
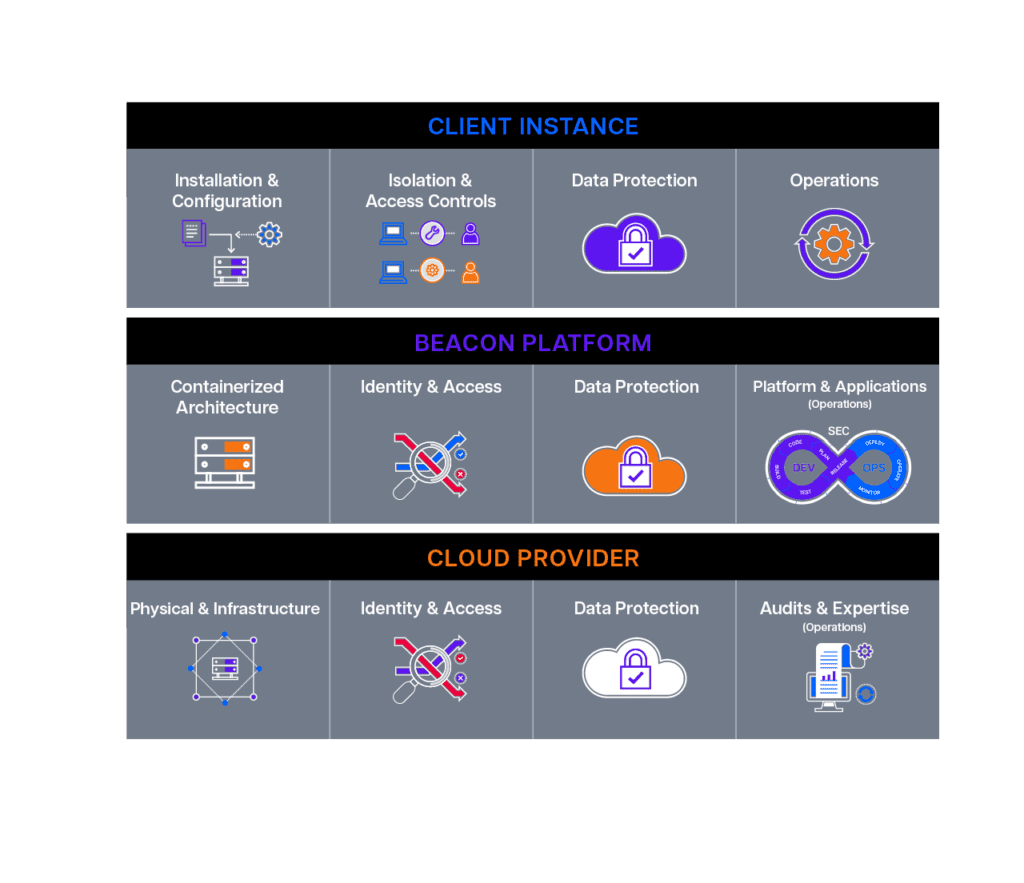
Each Beacon instance is installed directly into a customer’s own cloud account, virtual private cloud, or as a segregated but Beacon-managed domain. Security of each instance is delivered with a layered architecture that provides consistent installation, access controls, data protection, and automated processes. Customers are responsible for the security aspects of their individual and isolated instances, such as user roles and identities, data flow, and custom development, using a combination of Beacon components and existing corporate security processes and tools. This includes:
Beacon is responsible for the virtual machine images, code, containers, data encryption, and some configurations within the cloud infrastructure that each customer uses in their individual, isolated Platform instances. This includes:
The cloud provider is responsible for security of the cloud infrastructure, including physical equipment and locations, identity and access controls, and the software that delivers the compute, storage, database, and networking functionality. This includes:
Confident in the security and flexibility of our cloud infrastructure, our capital markets clients are maximizing the power of their full technology stack while building industry-leading applications, analytics, and reports, and scaling securely in the cloud.
News and perspectives on how our security build confidence while enhancing productivity and speeding time to market for financial services firms
© 2025 Beacon Platform Inc., a Clearwater Analytics company.
All rights reserved.